Advanced IP Blocker
A complete WordPress security firewall: blocks IPs, bots & countries. Includes an intelligent WAF, Threat Scoring, Geo-Challenge, 2FA, and Anti-Sp …
Plugin info
Maintenance & Compatibility
Maintenance score
Actively maintained • Last updated 74 days ago • Support resolved 100% • 4 reviews
Is Advanced IP Blocker abandoned?
Likely maintained (last update 74 days ago).
Compatibility
Similar & Alternatives
Explore plugins with similar tags, and compare key metrics like downloads, ratings, updates, support, and WP/PHP compatibility.
Description
Advanced IP Blocker is your all-in-one security solution to safeguard your WordPress website from a wide range of threats. This plugin provides a comprehensive suite of tools to automatically detect and block malicious activity, including brute-force attacks, vulnerability scanning, and spam bots. With its intuitive interface, you can easily manage whitelists, blocklists, and view detailed security logs to understand exactly how your site is being protected.
Important Note on PHP Version:
To ensure maximum security and access to all features, we strongly recommend using PHP 8.1 or higher. Some advanced features (like the local MaxMind database or full 2FA management via WP-CLI) require PHP 8.1.
Key Features:
* NEW: Server IP Reputation Check. Instantly audit your web server’s IP address against major blacklists (Spamhaus, AbuseIPDB) to diagnose SEO and email delivery issues.
* **NEW: Site Health & Vulnerability Scanner. Audit your WordPress environment instantly. Detects outdated plugins, insecure PHP versions, and checks your installed plugins against a database of 30,000+ known vulnerabilities.
* **PERFORMANCE BOOST: High-Speed Community Database. Migrated the “Community Defense Network” blocklist to a dedicated, indexed database table. This allows checking thousands of malicious IPs in microseconds with zero impact on site memory usage.
* **WordPress 6.9 Ready. Fully tested and compatible with the latest WordPress core update.
* **NEW: Community Defense Network. Join forces with other WordPress admins. The plugin now shares anonymous attack data to build a global, real-time blocklist of verified threats. Protect your site with community-powered intelligence.
* **NEW: Auto-Cleaning Logic. Smart expiration handling ensures your blocklists stay fresh and performant, automatically removing stale IPs from both the database and external firewalls (Cloudflare/.htaccess).
* **NEW: Cloud Edge Defense (Cloudflare). Connect your site directly to Cloudflare’s global network. Automatically sync your blocklists to the cloud to stop attackers before they reach your server. Zero server load protection.
* **NEW: Server-Level Firewall (.htaccess). Extreme performance upgrade. Write blocking rules and file hardening protections directly to your .htaccess file. Blocks threats instantly without loading PHP or WordPress.
* **NEW: IMPROVED: Smart Bot Verification. Enhanced logic to correctly identify legitimate traffic from iOS devices (iCloud Private Relay) and social media previews, eliminating false positives while keeping impostors out.
* **NEW: File Hardening. Protect your most sensitive files (wp-config.php, readme.html, .git) at the server level with a single click.
* NEW: AbuseIPDB Integration. Proactively block attackers before they strike. The plugin can now check visitor IPs against AbuseIPDB’s real-time, crowdsourced database of malicious IPs and block those with a high abuse score on their very first request.
* Edge Firewall Mode! Protect any PHP file or standalone application within your WordPress directory (even if it’s not part of WordPress). Ideal for securing custom scripts, legacy applications, or folders like /scan/. (Requires manual configuration).
* Advanced Rules Engine! Create powerful, custom security rules with multiple conditions (IP, Country, ASN, URI, User-Agent) and actions (Block, Challenge, or add Threat Score).
* Known Bot Verification. A powerful new security layer that uses reverse DNS lookups to verify legitimate crawlers like Googlebot and Bingbot. This completely neutralizes attackers who try to bypass security rules by faking their User-Agent, assigning high threat scores to impostors.
* Onboarding Setup Wizard. A brand new step-by-step wizard that guides new users through the essential security configurations (IP whitelisting, WAF, and bot traps) in under a minute, ensuring a strong security posture from day one.
* Major Refactor: Codebase Modernization. The entire plugin architecture has been refactored into a modern, modular structure. Logic for admin pages, AJAX, actions, and settings is now handled by dedicated classes, making the plugin more stable, performant, and easier to maintain and extend in the future.
* Advanced IP Spoofing Protection. A zero-trust “Trusted Proxies” system ensures the plugin always identifies the true visitor IP, even behind complex setups like Cloudflare or a custom reverse proxy. It neutralizes attacks that attempt to fake their IP, preventing block evasion and the framing of innocent users.
* Geo-Challenge. A smarter way to handle traffic from high-risk countries. Instead of a hard block, it presents a quick, invisible JavaScript challenge that stops bots but is seamless for human visitors. This reduces unwanted traffic without affecting potential legitimate users.
* ENHANCEMENT: Full Bulk-Action Support. IP management is now faster than ever. Both the Whitelist and the Blocked IPs list now support full bulk actions, allowing you to select and remove multiple entries at once, or unblock all IPs with a single click.
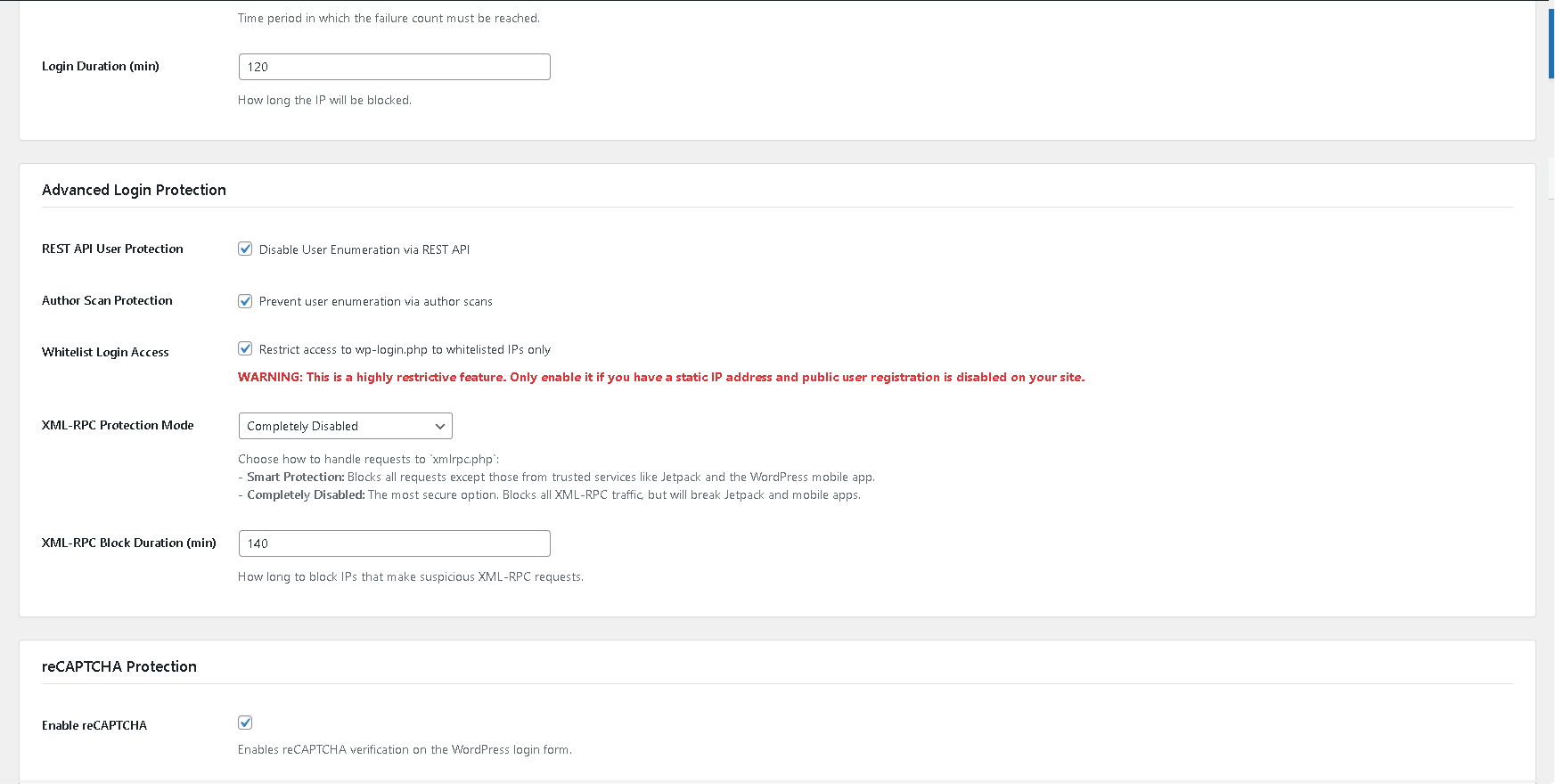
* Endpoint Lockdown Mode: Automatically shields wp-login.php and xmlrpc.php with a JavaScript challenge during sustained distributed attacks, preventing server overload.
* Two-Factor Authentication (2FA): Secure user accounts with industry-standard TOTP authentication, backup codes, role enforcement, and a central admin management dashboard.
* IP Trust & Threat Scoring System: An intelligent defense that assigns “threat points” to IPs for malicious actions, blocking them only when they reach a configurable score. More accurate and context-aware than simple rules.
* Attack Signature Engine (Beta): Proactively stops distributed botnet attacks by identifying and blocking the attacker’s “fingerprint” (signature) instead of just individual IPs.
* Web Application Firewall (WAF): Block malicious requests (SQLi, XSS, etc.) with a customizable ruleset.
* And much more: Rate Limiting, Country & ASN Blocking (with Spamhaus support), ASN Whitelisting, Push Notifications, Google reCAPTCHA, Honeypots, Active User Session Management, and Full WP-CLI Support.
Installation
- Upload the
advanced-ip-blockerfolder to the/wp-content/plugins/directory. - Activate the plugin through the ‘Plugins’ menu in WordPress.
- A new “Security” menu item will appear in your admin sidebar. All settings are located there.
- Crucial: Visit
Security > Dashboard > System Statusto ensure your IP and your server’s IP are whitelisted. Use the one-click buttons if they are not.
Frequently Asked Questions
The scanner checks your site in two ways:
Local Scan: Checks for outdated PHP versions, WordPress core updates, debug mode risks, and SSL status. This runs locally and instantly.
Deep Scan (Vulnerability Audit): Checks your installed plugins and themes against our central database of known security vulnerabilities (CVEs). This process is manual (you click a button) to ensure it never slows down your site during normal operation.
To ensure maximum performance as the network grows. Storing thousands of IPs in standard WordPress options (wp_options) can slow down a site. By moving this data to a dedicated, indexed database table (wp_advaipbl_community_ips), we ensure that lookups are lightning-fast (O(1) complexity) and consume negligible memory, regardless of how many threats we track.
It is a collaborative security feature where users share anonymized data about verified attacks (like SQL injections caught by the WAF or IPs flagged by AbuseIPDB). Our central server aggregates this data to create a global blocklist of active threats. You can choose to contribute data (“Join”) and/or use the global list to protect your site (“Enable Blocking”).
No. The data sharing happens in the background via a low-priority scheduled task (Cron) just a few times a day. The global blocklist is downloaded locally and cached, so checking an IP against it is instant (microseconds) and does not require external API calls.
You need a free Cloudflare account and your domain must be using Cloudflare’s nameservers.
1. Go to Security > Settings > Cloud Edge Defense.
2. Enter your Cloudflare API Token (with “Zone > Firewall Services > Edit” permissions) and Zone ID.
3. Click “Verify” and save.
The plugin will now automatically push your blocked IPs to Cloudflare’s Firewall. For a step-by-step guide with screenshots, click the help icon in the settings or visit our website.
Yes. Safety is our priority.
1. Backups: The plugin automatically creates a timestamped backup of your .htaccess file in a protected folder every time it writes new rules.
2. Compatibility: It automatically detects your server type and generates valid syntax for Apache 2.2 or 2.4.
3. Safety Limit: It includes a safety limit on the number of IPs written to the file to prevent server memory issues.
The “Server-Level Firewall (.htaccess)” feature relies on Apache/LiteSpeed specific files. If you use Nginx (without Apache), these local rules will be ignored by the server.
Recommendation: For Nginx users, we strongly recommend enabling the Cloud Edge Defense (Cloudflare) feature. It provides the same “pre-execution” blocking benefits but works on any server environment since the blocking happens in the cloud.
While every website’s security needs are unique, here is a general guide to get you started based on your site’s profile. For a deep dive into every feature, please consult our Comprehensive Feature Guide.
1. Essential First Steps (For ALL Websites)
No matter your site type, do these three things immediately after installation to ensure a strong baseline security without locking yourself out:
- Whitelist Your IPs: Go to
Security > Dashboard > System Statusand use the one-click buttons to add your current IP and your server’s IP to the whitelist. This is the most critical step. - Activate Trap Defenses: Go to
Security > Blocking Rules, and in the “User Agents” and “Honeypot URLs” tabs, copy the suggested lists into the active blocklist text areas. This provides immediate protection from thousands of common bots. - Enable Logging: Go to
Security > Settings > Generaland ensure “Enable Logging” is turned on. This gives you the visibility you need to understand what is happening on your site.
2. Recommended Profiles
Once the essentials are done, tailor the configuration to your site type:
For a Standard Blog or Business Website:
Your main goal is to block automated threats without affecting administrators.
* Enable the IP Trust & Threat Scoring System: This is the smartest way to block bad actors contextually. The default point values are an excellent starting point. (Found in Settings > IP Trust & Threat Scoring).
* Enable the WAF and Rate Limiting: These are powerful proactive defenses. (Found in Settings > Core Protections and Threshold Blocking).
* Enable Spamhaus ASN Protection: Let the plugin automatically block thousands of known malicious networks for you. (Found in Settings > Core Protections).
For an E-commerce or Membership Site (WooCommerce, etc.):
You need to protect your site while ensuring legitimate customers from around the world are never blocked.
* Enable Two-Factor Authentication (2FA): This is the single best way to protect administrator and shop manager accounts. Enforce it for these roles in Settings > Login & User Protection.
* Use Geo-Challenge Instead of Geoblocking: If you receive attacks from a specific country but also have customers there, use the Geo-Challenge feature instead of a hard block. This will stop bots without affecting human users.
* CRITICAL: DO NOT USE “Whitelist Login Access”. This feature will lock out your customers.
* WAF Exclusions: Double-check that URLs for your payment gateways (like Stripe or PayPal webhooks) are in the WAF exclusion list to ensure payments are processed correctly.
For Any Site Using a CDN or Reverse Proxy (like Cloudflare):
Your top priority is ensuring the plugin detects the correct visitor IP address.
* Configure Trusted Proxies: Go to Security > Settings > IP Detection. Add the IPs or, even better, the ASNs of your CDN/proxy service to this list. For Cloudflare, simply add AS13335 on a new line. This is essential for the accuracy of all other security features.
AbuseIPDB is a global, crowdsourced project that tracks and reports malicious IP addresses in real-time. Our new integration allows the plugin to check the reputation of a new, unknown visitor against this database on their first visit. If the IP has been recently reported by others for activities like hacking, spam, or brute-force attacks, and its “abuse confidence score” is above your configured threshold, the plugin will block it instantly. This acts as a proactive shield against known bad actors, stopping them before they even have a chance to test your defenses. You can enable it and add your free API key under Security > Settings > Threat Intelligence.
This is an advanced security feature that checks if visitors claiming to be from major search engines (like Googlebot) are legitimate. It performs a DNS lookup to verify their IP address. If the check fails, the visitor is identified as an “impersonator” and receives a high threat score, preventing them from exploiting the trust given to real crawlers. This feature is enabled by default under Settings > Core Protections.
This is a critical security feature that prevents IP spoofing. If your site is behind a service like Cloudflare, Varnish, or another reverse proxy, the server’s direct connection IP (REMOTE_ADDR) will always be the proxy’s IP, not the visitor’s. The real visitor IP is sent in an HTTP header (e.g., CF-Connecting-IP). An attacker can fake this header. The “Trusted Proxies” setting tells the plugin: “Only trust these headers if the request comes from an IP address I know is my proxy.” You can add IPs, CIDR ranges, or ASNs (like AS13335 for Cloudflare) to this list under Security > Settings > IP Detection.
Geoblocking is a hard block. It shows a “403 Access Denied” page to visitors from selected countries.
Geo-Challenge is a soft block. It shows a quick, automated JavaScript test to visitors from selected countries. Legitimate humans pass instantly, while most bots are stopped. This is useful for regions you are suspicious of but do not want to block entirely. You can, for example, block Country A and challenge Country B. You can configure it in Security > Settings > Core Protections.
The JavaScript challenge (used by Geo-Challenge, Signature Engine, and Endpoint Lockdown) requires dynamic content. Aggressive page caching can interfere with it. If you experience issues (like a challenge loop or a “Verification failed” error), you must configure your caching plugin (e.g., WP Rocket, WP Fastest Cache, LiteSpeed Cache) to NOT cache pages for visitors who do not have the advaipbl_js_verified cookie. Most caching plugins have a setting like “Never cache pages that use this cookie.”
Cookie consent plugins (like CookieYes) may block our security cookie from being set. To fix this, you must go into your cookie plugin’s settings and classify the cookie named advaipbl_js_verified as “Strictly Necessary” or “Essential”. This will allow the security challenge to function correctly.
For maximum performance, the plugin offers two ways to identify an IP’s location (Security > Settings > Geolocation):
1. Real-time API (Default): Easy to set up and great for most websites.
2. Local Database (Highest Performance): Downloads the MaxMind GeoLite2 database to your server for instant, offline lookups with zero external API calls. Recommended for high-traffic sites. Requires a free MaxMind license key.
- Admin: Go to
Security > Settings > Login & User Protectionand enable 2FA globally. You can also enforce it for specific user roles. - User: Go to your WordPress Profile page. You will find a new section to set up 2FA by scanning a QR code with an authenticator app and saving your backup codes.
This is an advanced defense that stops botnets by blocking the attacker’s “fingerprint” (signature), not just their IP. It works in three phases you can enable in Security > Settings > Signature Engine: Logging, Analysis (a background task that finds patterns), and Blocking (presents a JS challenge to malicious signatures). You can manage detected signatures in IP Management > Blocked Signatures.
Think of them as three layers of defense:
1. WAF (Web Application Firewall): The simplest layer. It blocks requests based on simple malicious patterns (e.g., union select). It’s fast and stops common, generic attacks.
2. Attack Signature Engine: The automated layer. It looks for patterns of attack from many different IPs (botnets) and blocks the attack’s “fingerprint” (signature) for all visitors. You don’t create these rules; the plugin does.
3. Advanced Rules Engine: The manual control layer. This is where you build your own specific, multi-conditional rules. For example: “IF the visitor is from China AND is trying to access /wp-admin/ THEN Block them permanently.” It gives you the ultimate power to create a security policy tailored exactly to your site’s needs.
This plugin includes an advanced “Edge Firewall Mode” that allows you to extend its protection to any PHP script on your server. This is perfect for securing custom applications or directories that are not managed by WordPress. To enable it, you need to add a single line of code to the beginning of the PHP file you want to protect. This manual step ensures that the protection is explicit and works on any server environment. For a complete step-by-step guide, please see our documentation: How to Protect Non-WordPress Folders.
Review feed
Screenshots
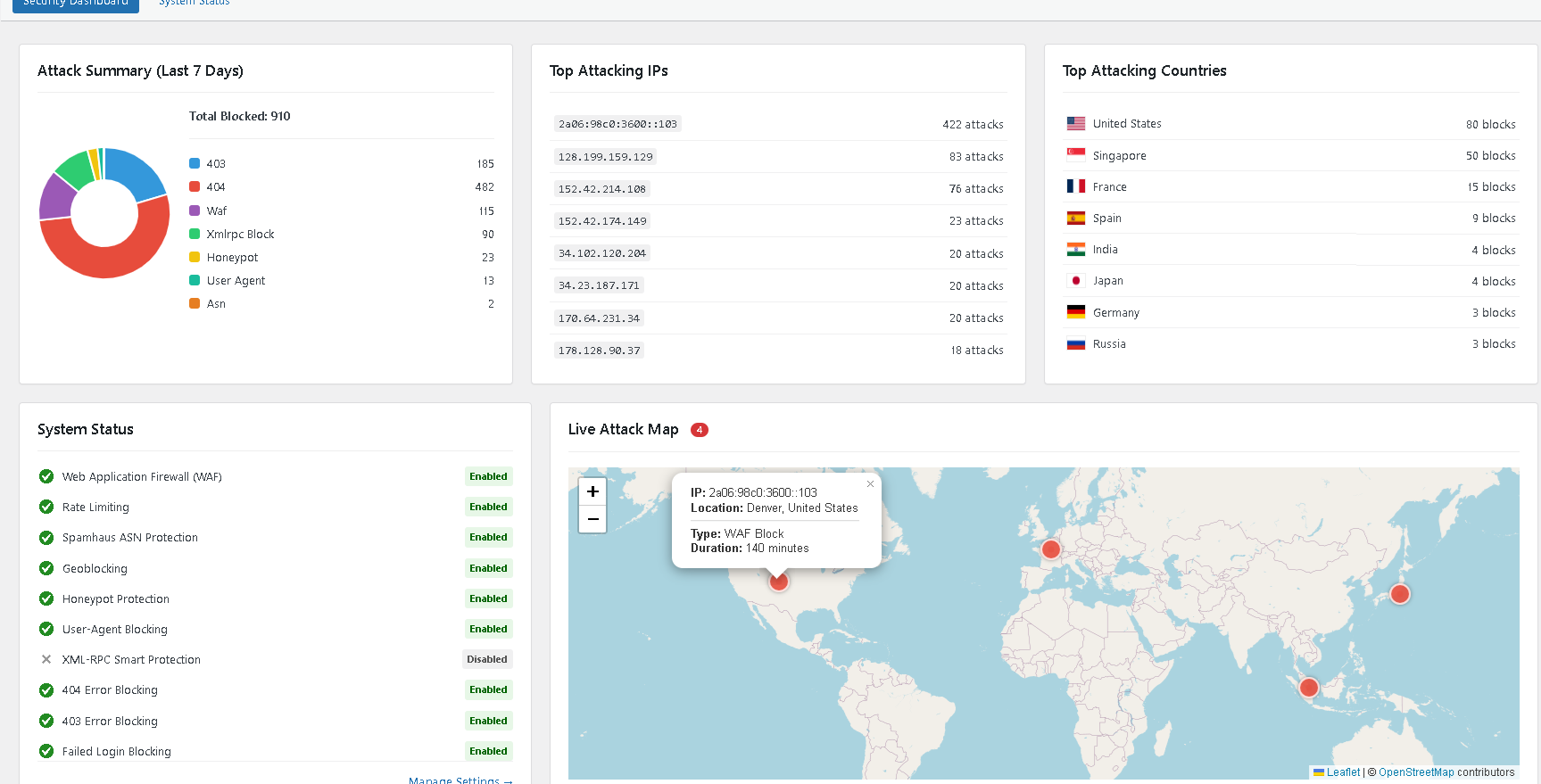
The new Security Dashboard with real-time charts and a Live Attack Map.
Modern and intuitive two-level navigation system for easy access to all features.
The main Settings page to configure all protection modules like WAF and Rate Limiting.
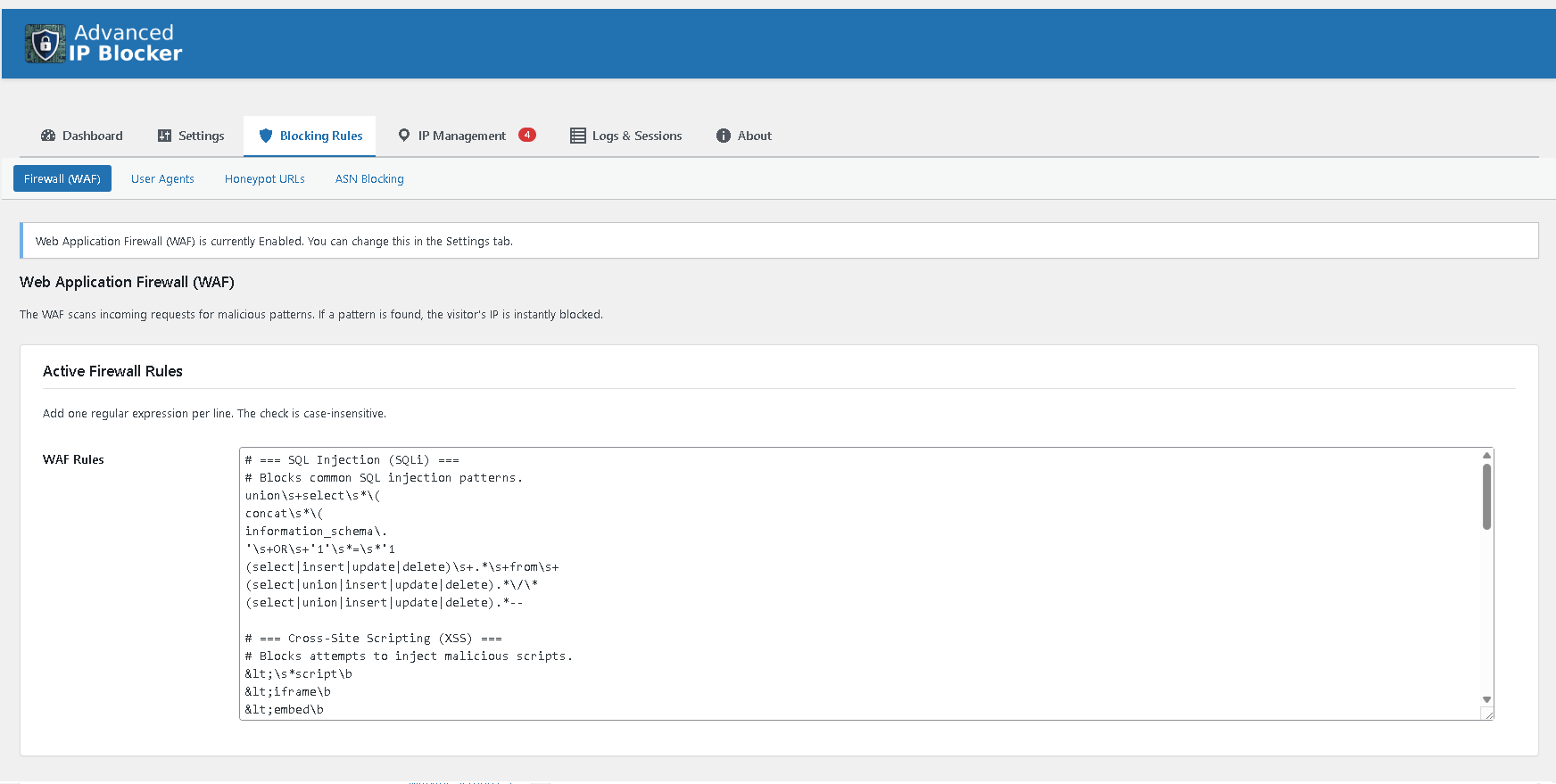
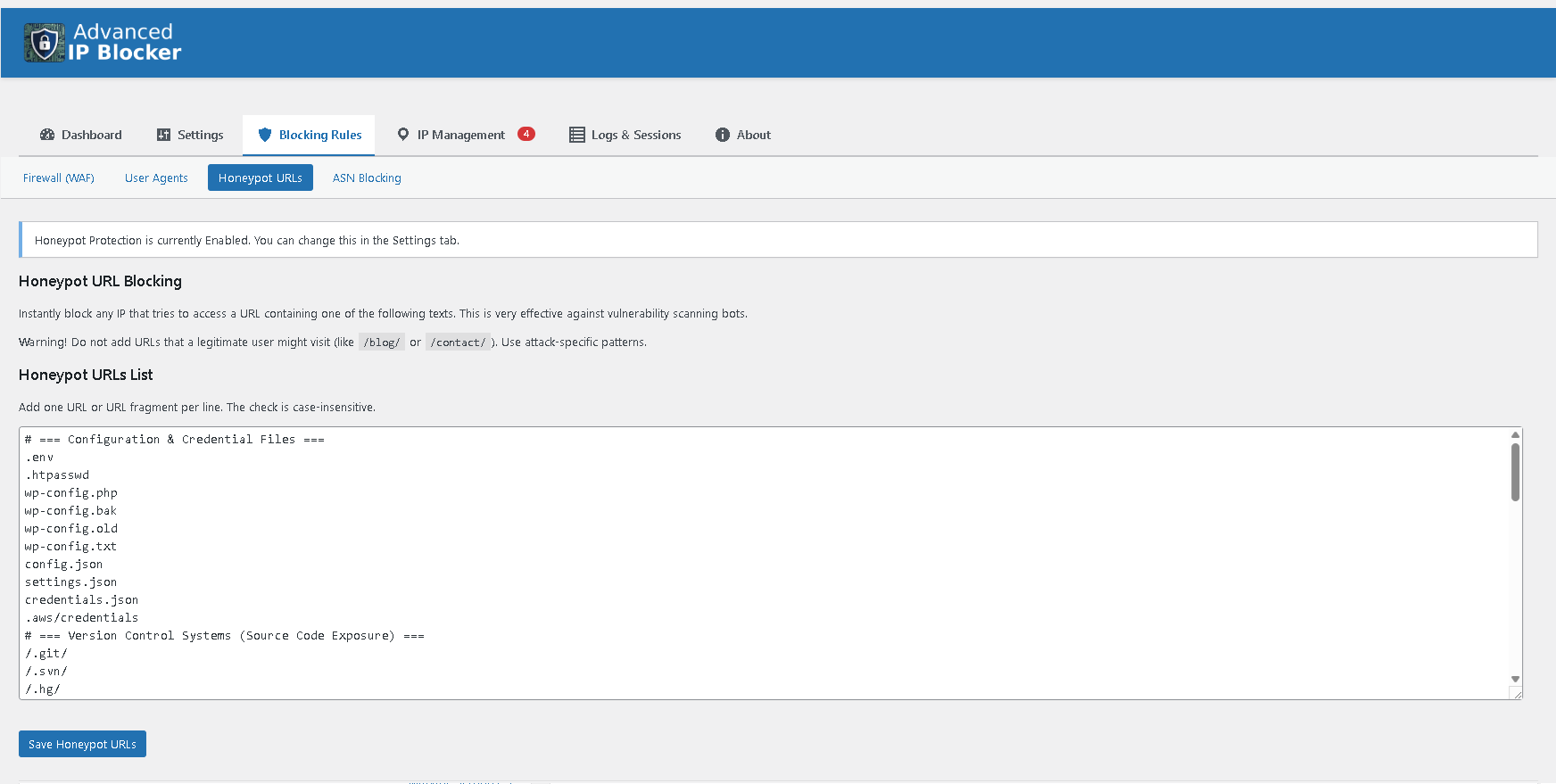
Powerful Web Application Firewall (WAF) with recommended rules.
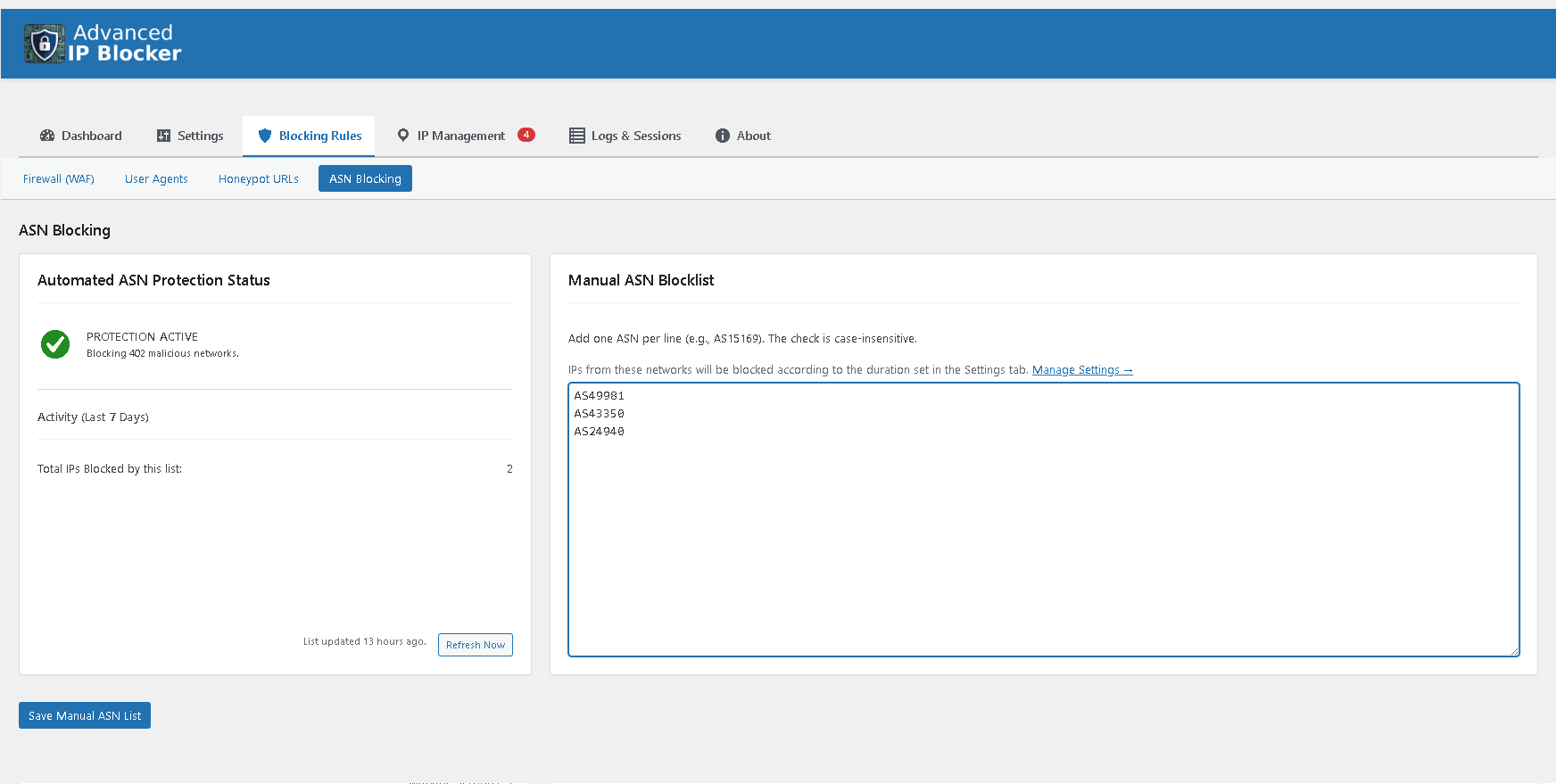
Block entire networks with ASN Blocking, powered by the Spamhaus list.
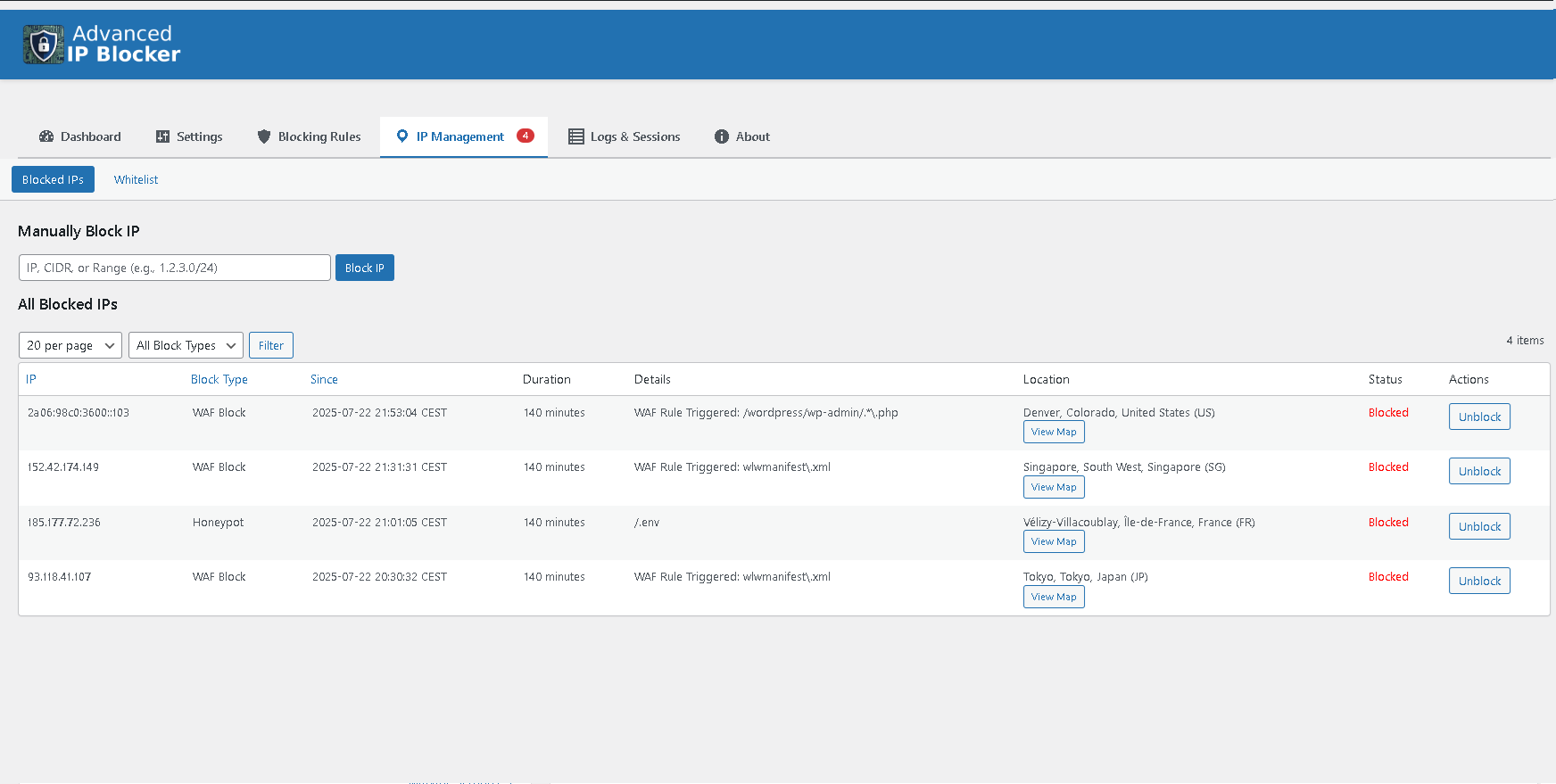
Detailed Blocked IPs table with the "View Map" modal in action.
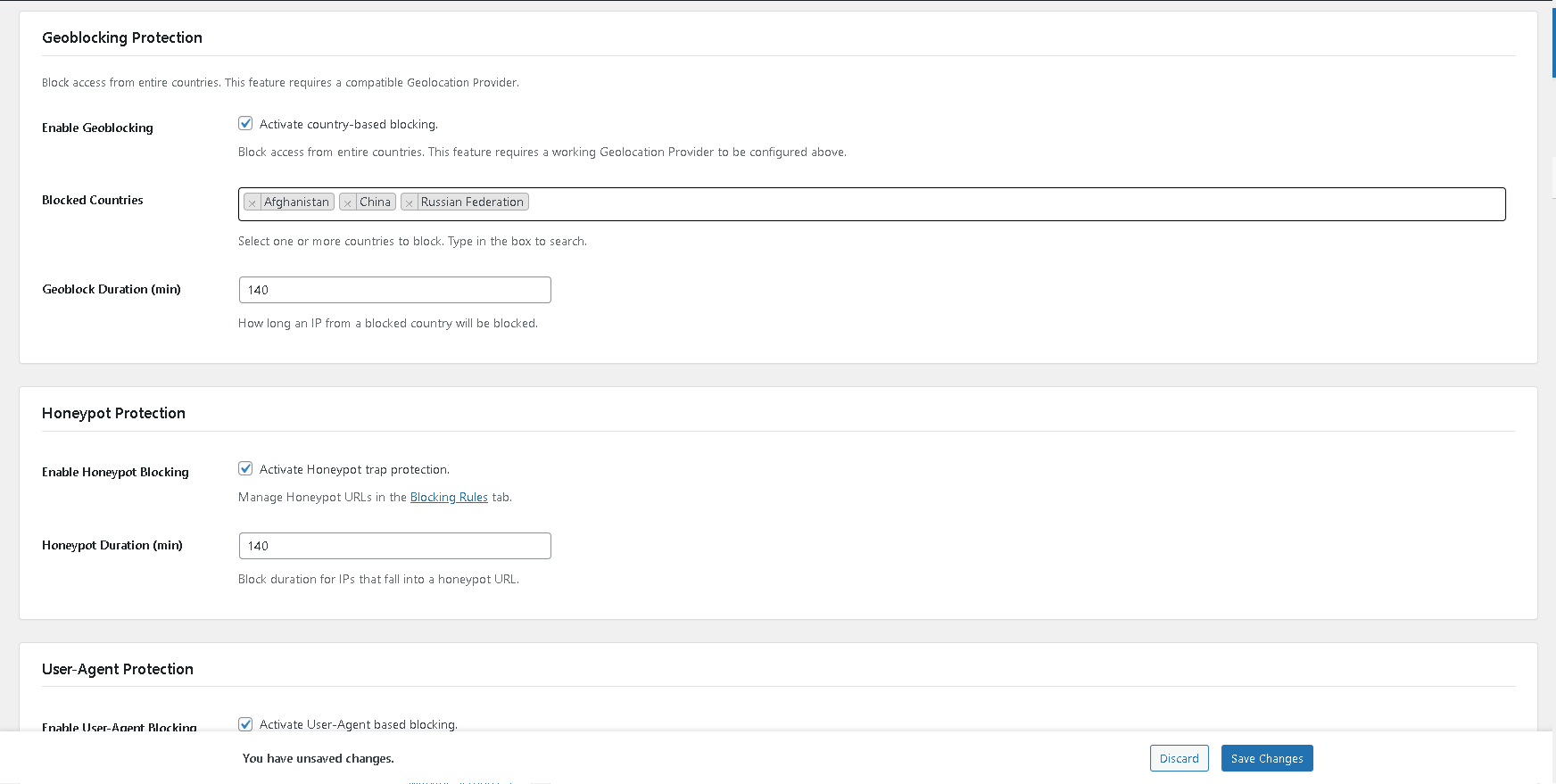
Country Blocking (Geoblocking) and Geo-Challenge with user-friendly selectors and smart warnings.
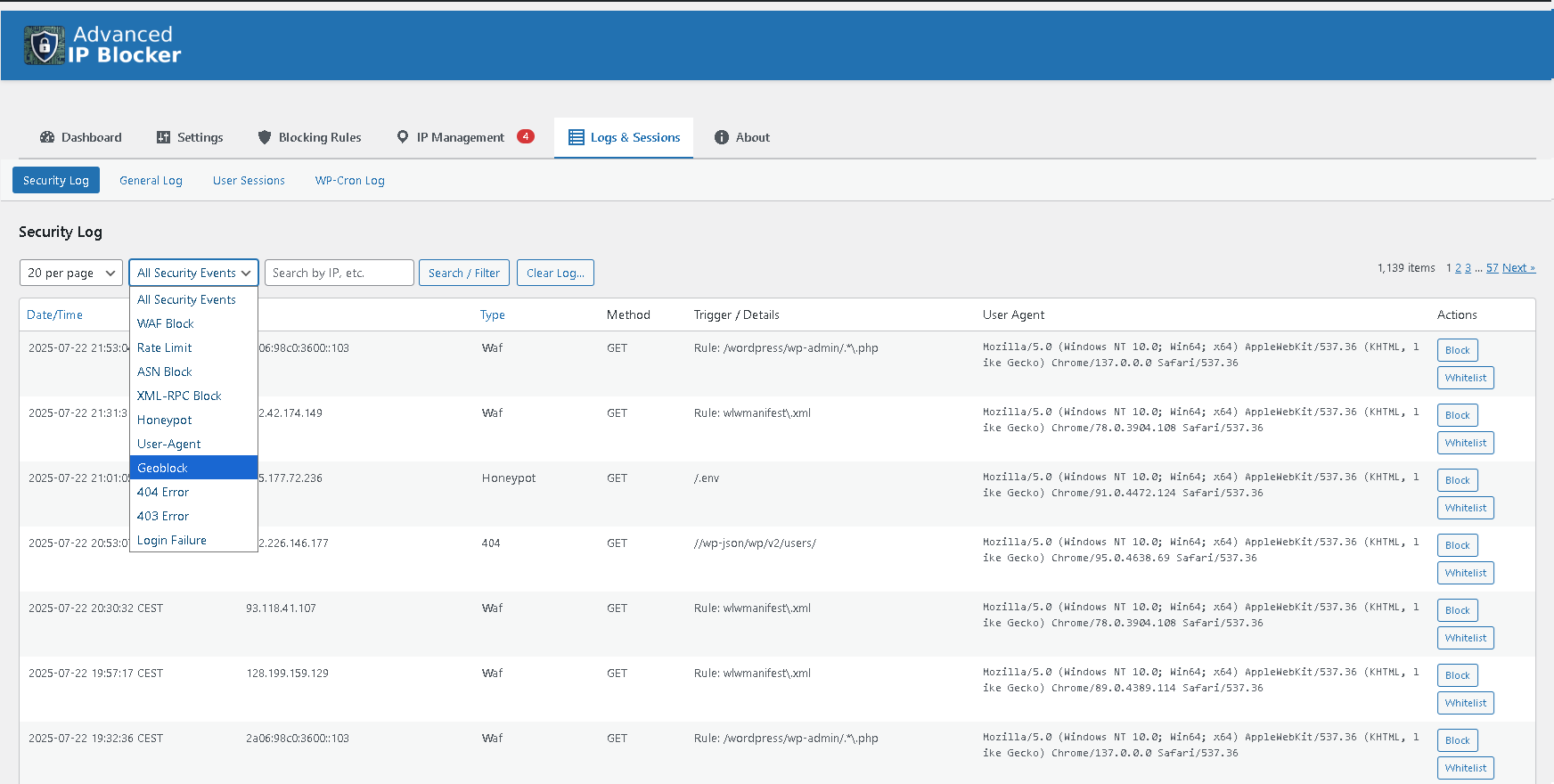
Unified Security Log with a powerful filter to analyze all attack events.
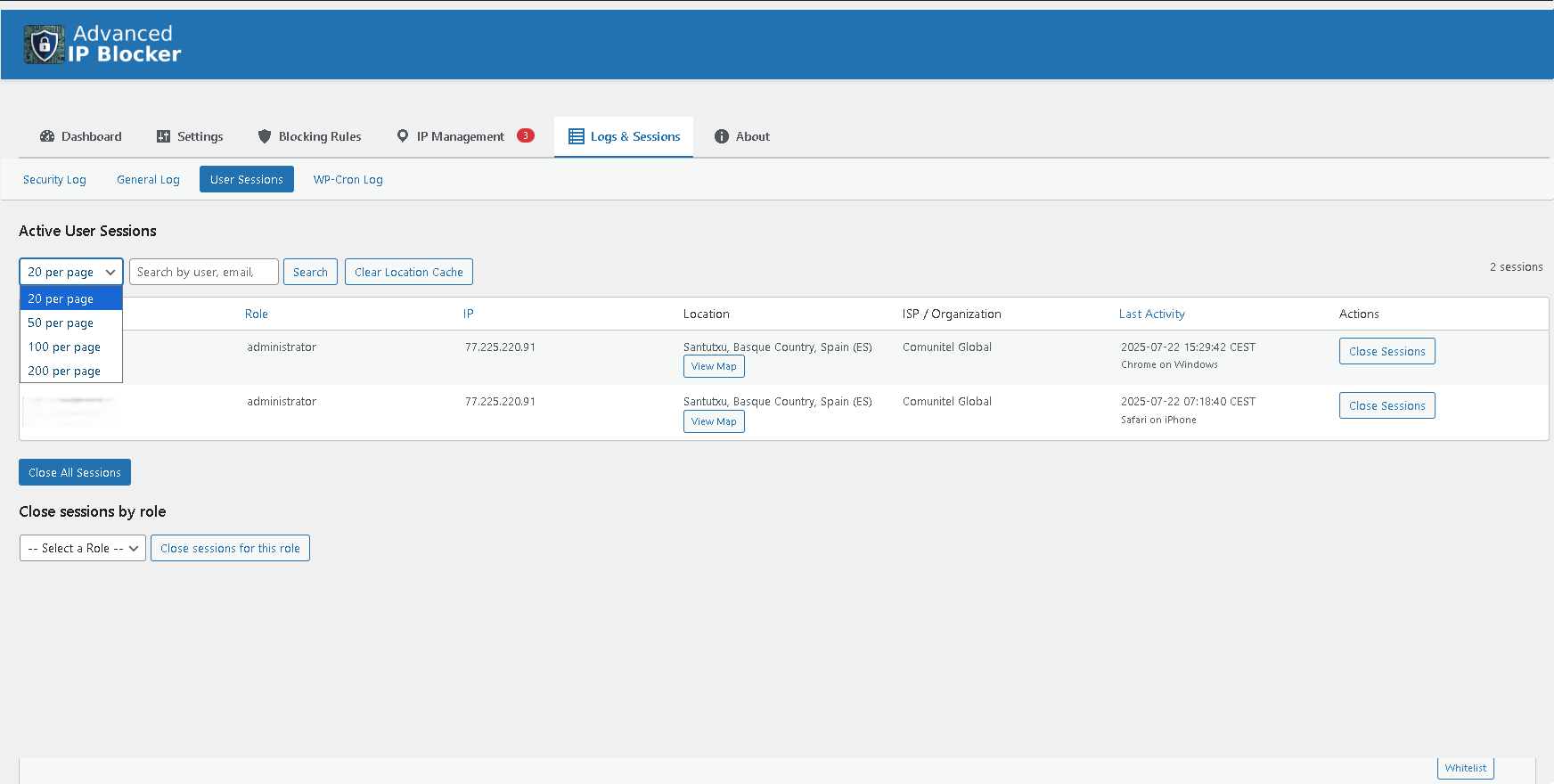
Active User Session Management to monitor and terminate logged-in users.
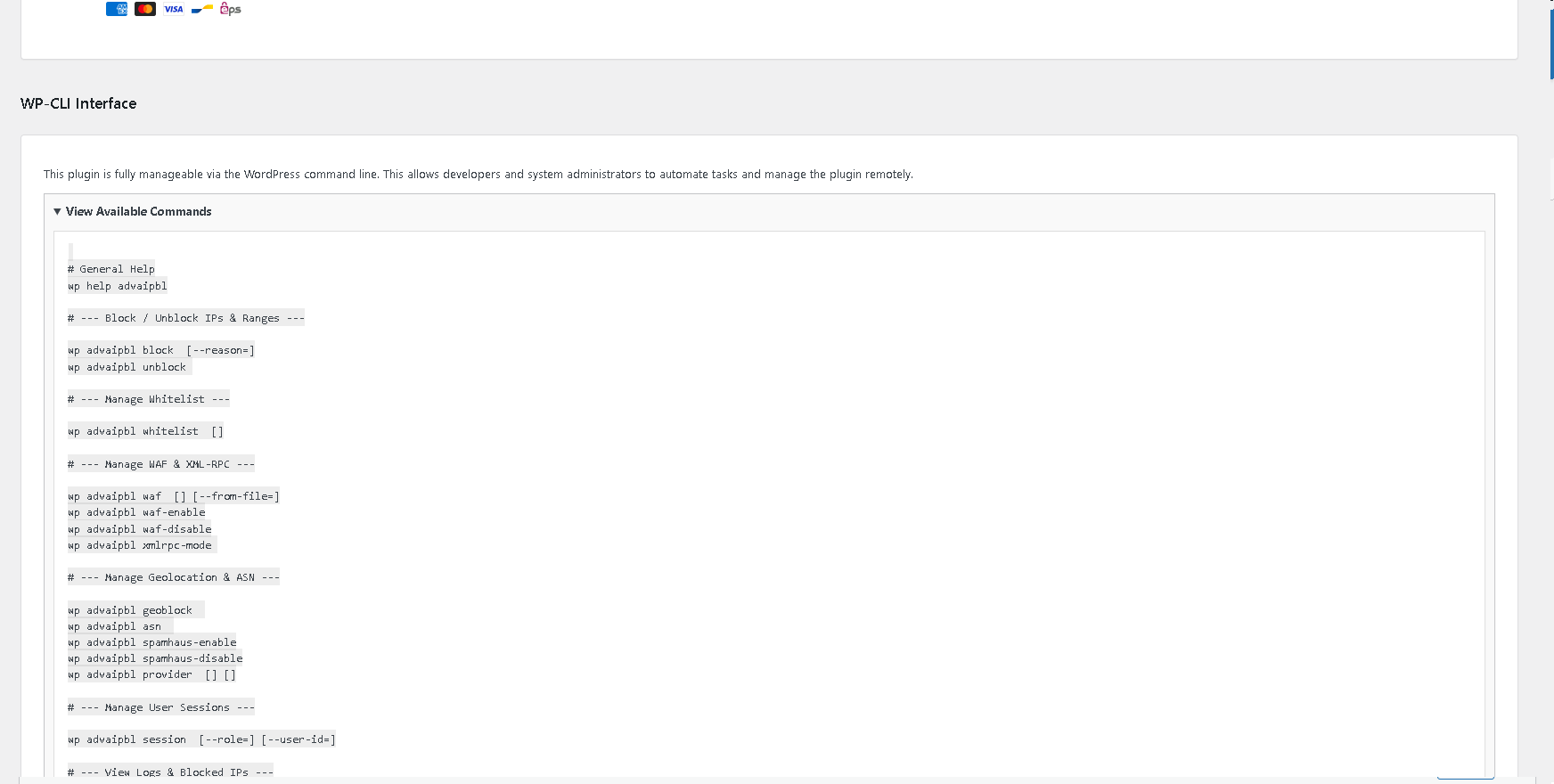
Full WP-CLI support documentation, accessible from the "About" tab.
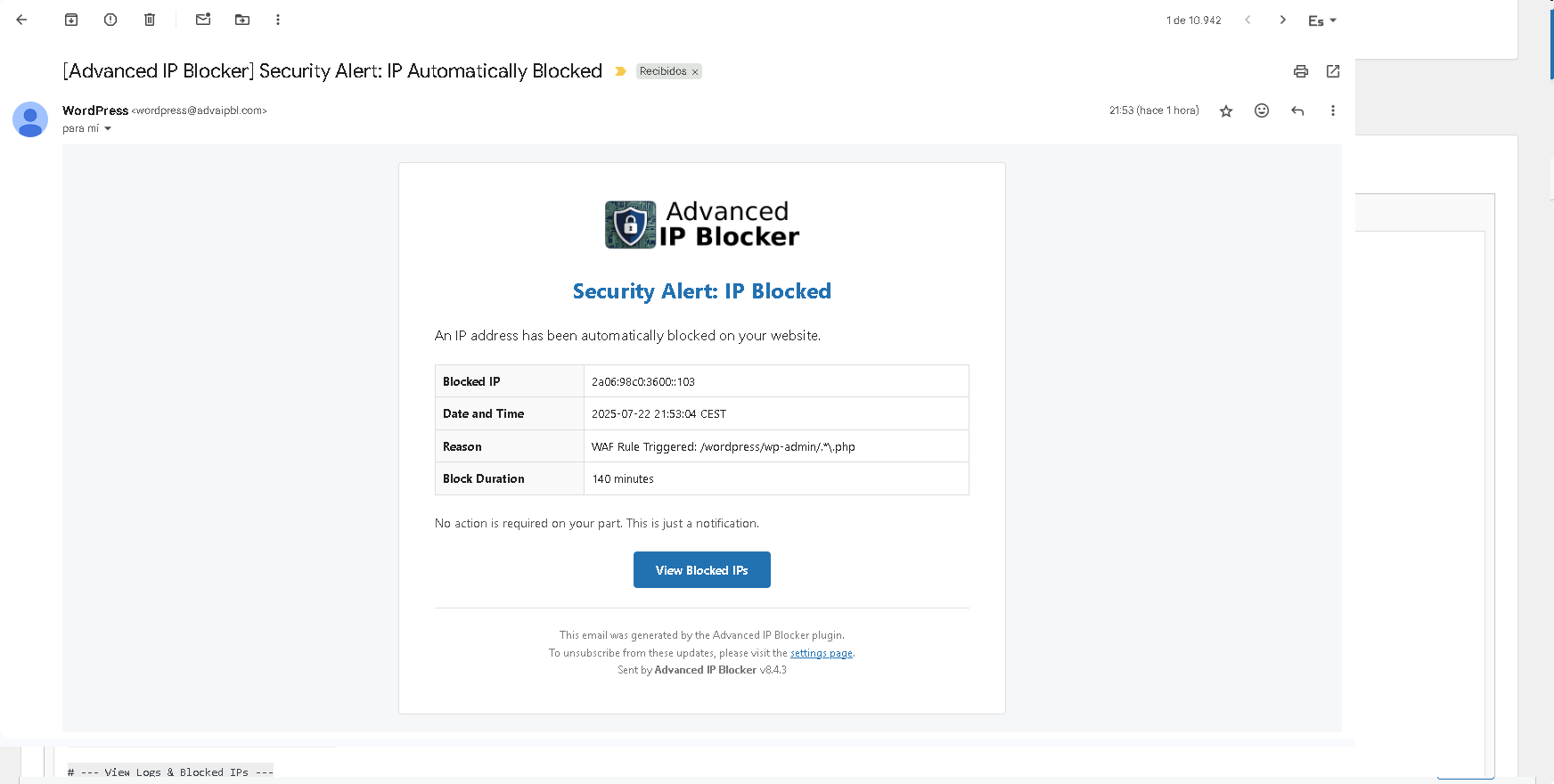
An example of a professional HTML email notification.
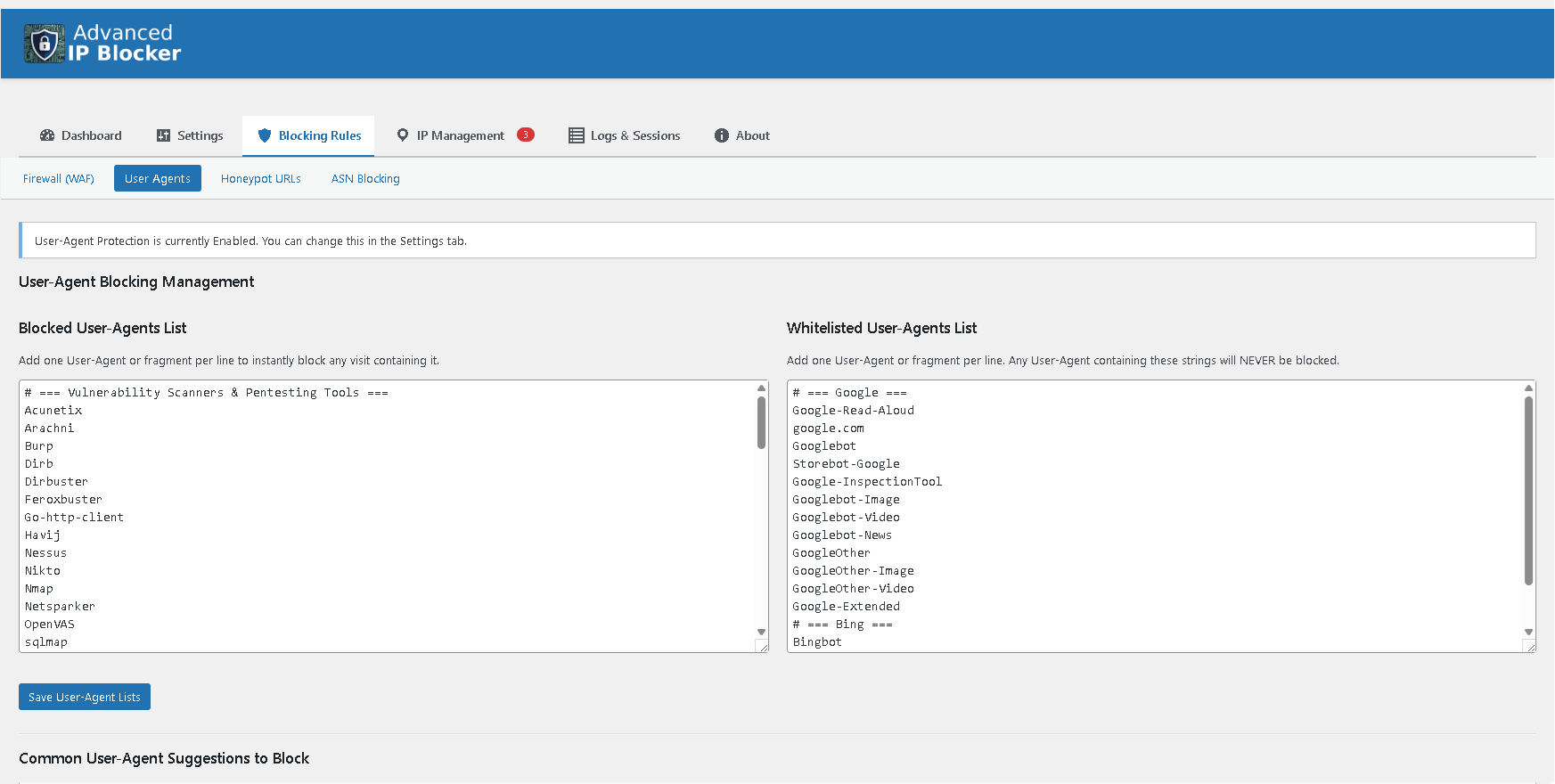
The new "Trusted Proxies" setting for advanced anti-spoofing protection.
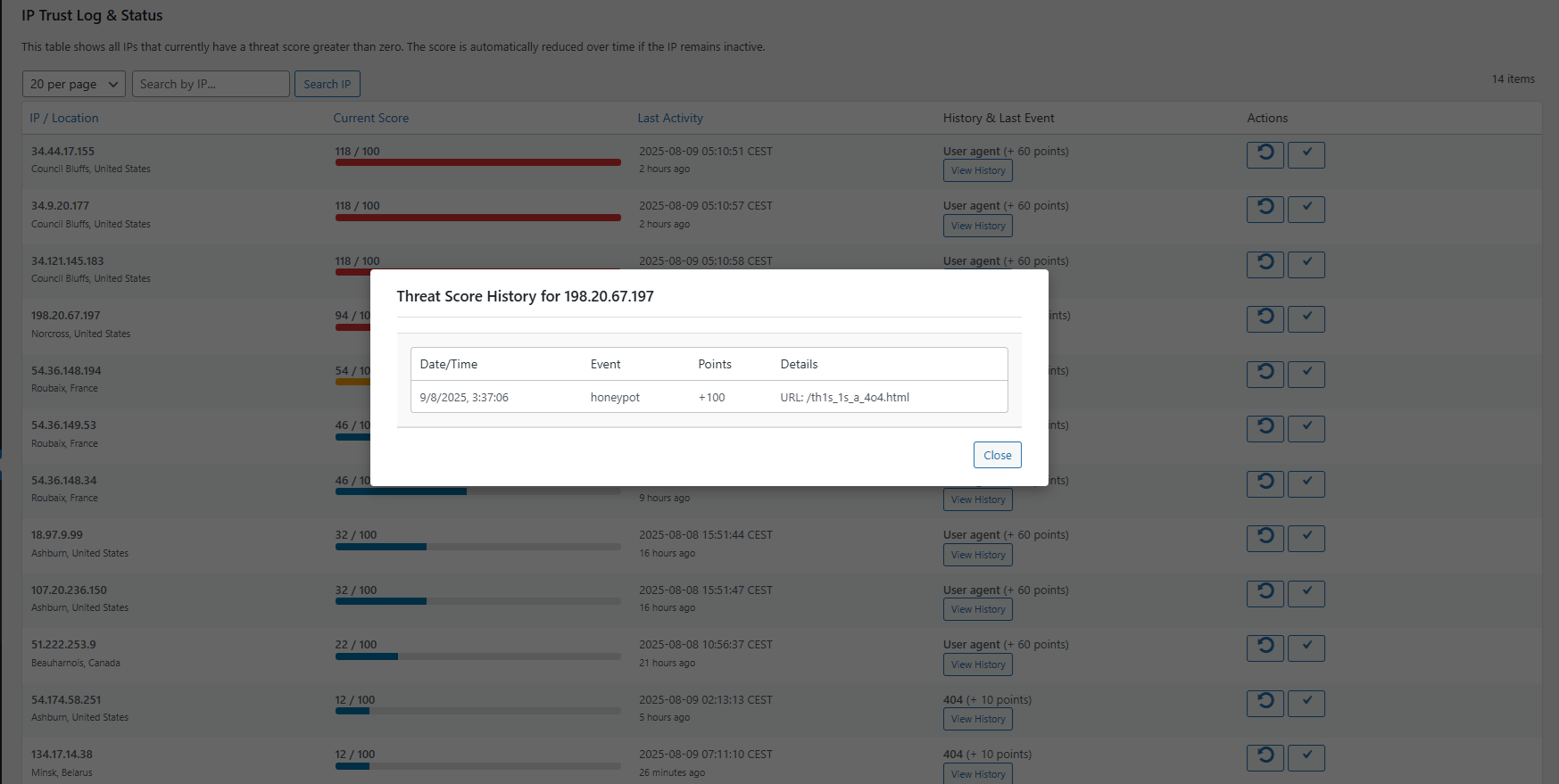
IP Trust & Threat Scoring System.
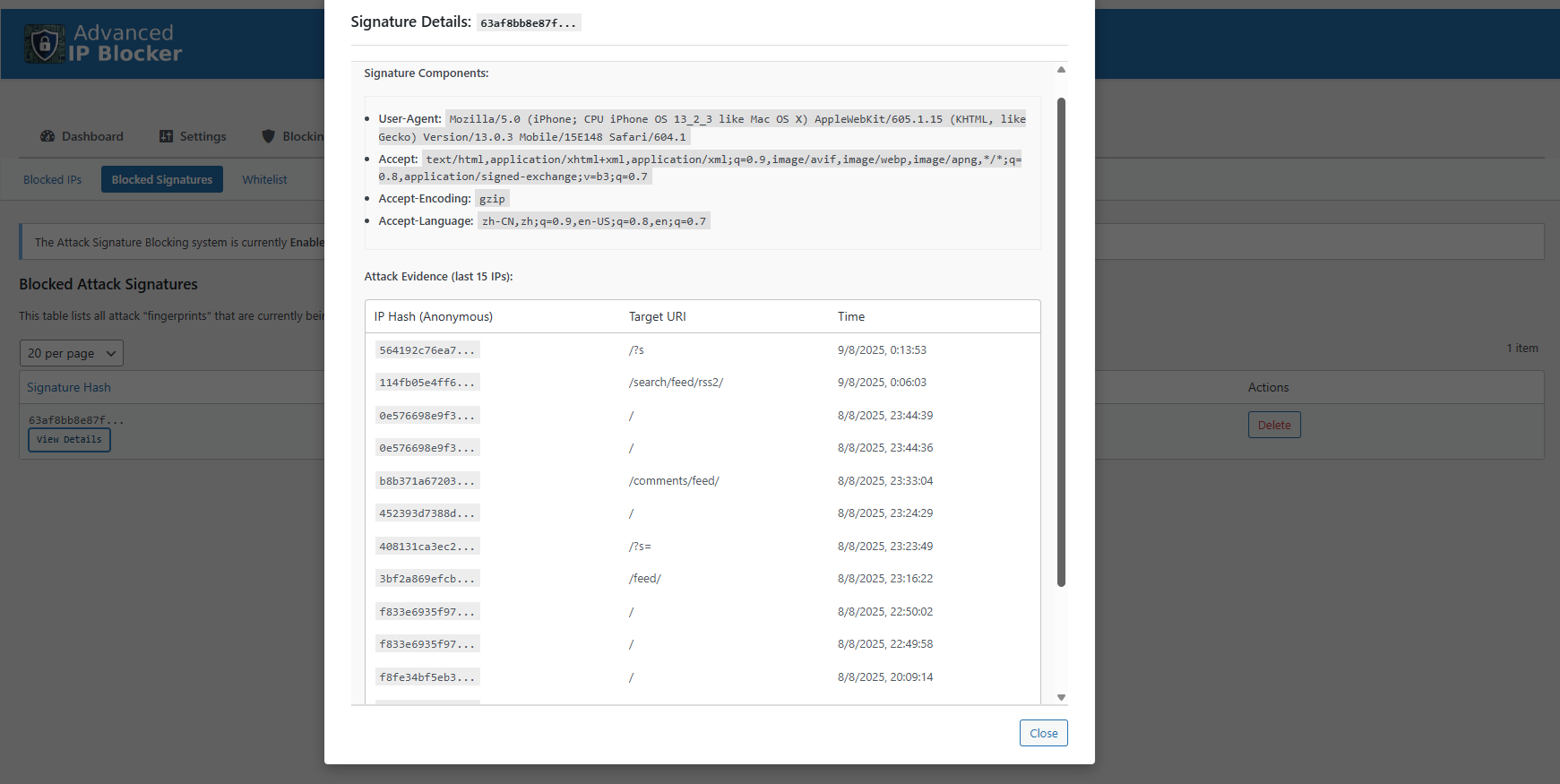
Attack Signature Engine (Beta).
Changelog
8.6.4
- **Critical Fix (Performance): Resolved a bug where the “Community List Update” cron job could be scheduled multiple times, causing excessive background tasks. This update automatically cleans up duplicate events.
- **NEW FEATURE: Server Reputation Scanner. Added a tool in the “Site Scanner” tab to check if your server’s IP address is blacklisted by Spamhaus or AbuseIPDB, helping you identify hosting-related issues.
- **Improvement: Optimized the cron scheduling logic to prevent future duplication of tasks.
- **Improvement: Enhanced the Site Scanner UI with clearer status indicators and action buttons.
8.6.3
- **NEW MAJOR FEATURE: Site Health & Vulnerability Scanner. Added a comprehensive security audit tool. It checks for critical issues like outdated PHP, debug mode risks, and scans your plugins/themes against a database of 30,000+ known vulnerabilities.
- **Architecture Upgrade: Migrated the “Community Defense Network” IP list to a dedicated custom database table for extreme performance and scalability. This eliminates memory overhead even with thousands of blocked IPs.
- **Compatibility: Verified full compatibility with WordPress 6.9.
- **UI Enhancement: Added help icons and direct documentation links to advanced settings for easier configuration.
- **Improvement: The setup wizard now automatically enables the Server-Level Firewall (.htaccess) for stronger default protection.
8.6.2
- **NEW MAJOR FEATURE: Community Defense Network (Beta). Launched our collaborative threat intelligence network. You can now opt-in to share anonymized attack reports and protect your site with a global blocklist generated from verified community data.
- **Enhancement: Increased default block duration to 24 hours (1440 mins) for stronger protection and better data quality for the community network.
- **Performance: Optimized the wp_options storage for the community blocklist to prevent autoloading, ensuring zero impact on site load time.
- **Security Hardening: Updated default WAF rules to include protection against Scrapy, Go-http-client, and common log/backup file scanners (.sql, .log).
- **Improvement: The “Clean Expired IPs” cron job now automatically syncs removals with Cloudflare and Htaccess, ensuring that temporary bans are lifted correctly across all firewalls.
- **Fix: Resolved a display issue where the “Settings” tab content could be malformed if certain options were disabled.
8.6.1
- **NEW MAJOR FEATURE: Cloud Edge Defense. Introducing cloud-based blocking. Integrate seamlessly with Cloudflare to sync your “Manually Blocked” and “Permanent” IPs directly to the Cloudflare Firewall (WAF). This stops attackers at the network edge, reducing server load to zero.
- **NEW MAJOR FEATURE: Server-Level Firewall. Added a high-performance module that writes blocking rules and file hardening directives (wp-config.php, .git, etc.) directly to your .htaccess file. Includes automatic backups and dual-stack Apache support.
- **Critical Fix: Resolved a false positive issue affecting legitimate iOS users (iCloud Private Relay) and social media link previews, which were incorrectly flagged as “Bot Impersonators”.
- **Enhancement: Completely redesigned the Settings experience with a new “Help Center” approach, providing direct links to documentation for complex features.
- **Enhancement: Updated the Setup Wizard to include Server-Level Firewall activation and better guidance for advanced integrations.
- **Performance: Optimized the IP blocking logic to handle bulk actions efficiently by updating external firewalls (Htaccess/Cloudflare) only once per batch.
- **Telemetría: Updated data points to track adoption of Cloudflare and Htaccess features.
8.6.0
- NEW MAJOR FEATURE: Server-Level Firewall (.htaccess). Introducing the ultimate performance upgrade. You can now write blocking rules directly to your server’s
.htaccessfile. This blocks threats before WordPress loads, saving massive server resources. Includes automatic backups, proxy awareness (SetEnvIF), and support for Apache 2.2/2.4. - Feature: File Hardening. Easily block access to sensitive system files (
wp-config.php,readme.html, etc.) at the server level. - Feature: Auto-Synchronization. Automatically syncs your “Manually Blocked” and “Permanent” IPs from the database to the server firewall.
- Feature: Temporary Block Offloading. Optionally push temporary blocks (like 404 abusers or failed logins) to the server firewall for the duration of their ban.
- Critical Fix: Bot Verification. Resolved a false positive issue where legitimate iOS users (using iCloud Private Relay) or social media app browsers (Instagram/Facebook in-app) were being blocked as “Bot Impersonators”. The verification logic has been refined to exclude social bots from strict DNS checks while maintaining security for search engine crawlers.
- Enhancement: Updated Telemetry receiver to track the adoption of the new firewall features.
- UI/UX: Integrated the new firewall controls into the main Settings tab for a streamlined experience.
8.5.15
- Critical Fix: Resolved a fatal error (
TypeError) that could occur during GeoIP lookups with the local MaxMind database, particularly on PHP 8.3+. The GeoIP manager is now more resilient to potential database read errors. - Fix: Corrected a
class not foundfatal error that could occur when using the “Edge Firewall Mode” to protect non-WordPress files, ensuring the autoloader for external libraries is correctly registered. - Fix: Addressed a
Failed opening requiredfatal error by making the plugin’s internal file path resolution more robust. - Fix: The “Local Database Status” field in the Geolocation settings will no longer cause a fatal error if the local database method is not active.
- Dev: Addressed several
ERRORlevel notifications from the WordPress.org Plugin Check tool related to database query preparation and variable naming conventions.
8.5.14
- Major Stability Fix: Implemented robust error handling for the MaxMind local database integration. The plugin will no longer cause a fatal error if the GeoIP database file is corrupt or unreadable, ensuring site stability.
- Enhancement: Geolocation data (Country/City) will now be displayed in the Security Log for all relevant events, including warnings like Challenges, not just for critical blocks. This provides administrators with better context for all security events when using the local MaxMind database.
- Security: Added a secure, IP-whitelisted internal endpoint for integration with external monitoring tools.
- Dev: General code maintenance and improvements to the plugin’s core stability.
8.5.13
- NEW MAJOR FEATURE: AbuseIPDB Integration. Added a powerful new security layer to proactively block known malicious IPs by checking their reputation against the real-time AbuseIPDB threat database. This feature can be enabled in a new “Threat Intelligence” section in the settings and requires a free API key.
- Enhancement: The AbuseIPDB integration is resilient, featuring a “circuit breaker” that temporarily pauses API calls if the daily quota is exceeded or the service is unavailable, preventing errors and log spam.
- Enhancement: Improved the “Live Security Feed” to show more descriptive details for blocks originating from AbuseIPDB, Advanced Rules, and the WAF.
- Enhancement: Added the new AbuseIPDB status to the main Security Dashboard and the Telemetry data.
8.5.12
- Major Performance Enhancement: Refactored the caching compatibility logic to resolve a critical issue with LiteSpeed Cache (LSCWP) and other page caching plugins. The
DONOTCACHEPAGEconstant is now only defined when a JavaScript challenge is actively being served, allowing all other pages to be cached correctly. This significantly improves performance for all sites using page caching. (A big thank you to user Moddo from the WordPress.org forums for their detailed bug report!) - Enhancement: Improved the sanitization and validation of the WAF (Web Application Firewall) rules. The system now automatically removes duplicate rules and discards invalid regular expressions upon saving, preventing potential errors and improving usability.
- Enhancement: Added a prominent warning to the WAF configuration page to caution users against creating overly broad rules that could cause a site lockout.
- Fix: The custom block message now correctly renders basic HTML tags (
<h1>,<br>), allowing for better formatted and more professional-looking block pages. - Fix: Resolved an issue where the “Completely Disabled” mode for XML-RPC would result in a blank page instead of a proper 403 Forbidden error response.
8.5.11
- NEW MAJOR FEATURE: Edge Firewall Mode. The plugin’s full security suite (WAF, Advanced Rules, Challenges, Threat Scoring) can now be extended to protect any standalone PHP script or application within your WordPress installation. This requires a manual one-line code addition to the file you wish to protect.
- Enhancement: The “Advanced Rules Engine” now includes robust data sanitization and validation, making custom rule creation even more secure.
- Enhancement: Improved the Admin Bar menu by adding separate counters for Blocked IPs, Signatures, and Endpoints, with a total count on the main menu items for better at-a-glance visibility.
- Enhancement: The “Verify Known Bots” feature now uses the “User-Agent” block duration as a fallback if the Threat Scoring system is disabled, ensuring impostor bots are always blocked.
- Fix: Resolved a critical bug where the JavaScript Challenge could enter an infinite loop in specific contexts, particularly with
xmlrpc.phplockdowns or when triggered by the Edge Firewall. - Fix: Corrected a fatal error (
Class "BaconQrCode..." not found) that occurred in limited environments likexmlrpc.phpor the new Edge Mode by implementing a more robust “lazy loading” for the 2FA module. - Fix: Solved an issue where the custom block message would not render HTML tags (
<h1>,<br>) correctly, now allowing for formatted block pages. - Fix: The “Smart Protection” mode for
xmlrpc.phpnow correctly blocks unauthorized users instead of showing a server error (503) in certain post-challenge scenarios. - Fix: Fixed a fatal error (
Undefined constant "ADVAIPBL_USM_...") that occurred when the Edge Firewall Mode was active. - Fix: Patched a fatal error in the “Whitelist Signature” AJAX function (
self::OPTION_SETTINGSscope issue).
8.5.10
- New: Advanced Rules Engine! Create powerful, custom security rules with multiple conditions (IP, Country, ASN, URI, User-Agent) and actions (Block, Challenge, or add Threat Score).
- Enhancement: Added ‘is not’ operator to ‘Country’ and ‘ASN’ conditions in the Advanced Rules Engine for more flexible rule creation.
- Enhancement: Added dependency status notices in the Advanced Rules tab to improve user experience.
- Fix: Resolved a loop issue in the JavaScript Challenge functionality when triggered by Advanced Rules.
- Fix: Corrected notification details (duration and reason) for blocks originating from Advanced Rules to ensure accuracy.
- Fix: Improved UI for the Advanced Rules constructor, especially the country selector within modals.
- Dev: Added foundation for future improvements to the Advanced Rules UI, such as pagination and bulk actions.
8.5.9 – The Foundation Update: Refactoring, Onboarding & Bot Verification
- NEW MAJOR FEATURE: Onboarding Setup Wizard. A new step-by-step wizard guides first-time users through the most critical security settings (IP whitelisting, WAF, bot traps), ensuring a strong security posture from the moment of activation.
- NEW MAJOR FEATURE: Known Bot Verification. A new security layer that uses reverse DNS to verify legitimate crawlers (Googlebot, Bingbot, etc.). This neutralizes attackers faking their User-Agent and assigns a high threat score to impostors.
- MAJOR REFACTOR: Complete Codebase Overhaul. The entire plugin has been refactored into a modern, modular, object-oriented structure. Logic for admin pages, AJAX handlers, action handlers, and settings management has been separated into dedicated classes. This significantly improves stability, performance, and long-term maintainability.
- Enhancement: The Import/Export feature is now more robust, correctly backing up and restoring the main blocked IPs table and automatically handling all plugin-related options for future-proof compatibility.
- Enhancement: Added comprehensive WP-CLI commands for all new features, including
trusted-proxy,geo-challenge,asn-whitelist,signature, andbot-verify. - Enhancement: Improved the user interface of the JavaScript challenge page, making it fully responsive and adding better user interaction with a timeout and manual verification option.
- Fix: Resolved a critical bug where the JavaScript challenge system could cause infinite loops or fail on sites with aggressive page caching (e.g., WP Rocket, WP Fastest Cache) or cookie consent (GDPR) plugins.
- Fix: Addressed multiple bugs in WP-CLI, including a fatal error on the
session listcommand and compatibility issues with PHP versions below 8.1.
8.5.8.1
- Fix: Corrected the
Tested up toversion in thereadme.txtfile to remove the “This plugin has not been tested with your current version of WordPress” warning. The plugin is fully compatible with the latest WordPress version. - Tweak: Updated and completed missing strings in the Spanish translation.
- Note: This version includes all the major features and enhancements from version 8.5.8, such as the new Trusted Proxies system and Geo-Challenge functionality.
8.5.8
- NEW MAJOR FEATURE: Advanced IP Spoofing Protection. Implemented a “Trusted Proxies” system to ensure accurate visitor IP detection behind services like Cloudflare or other reverse proxies. The plugin now operates on a zero-trust model, ignoring proxy headers from untrusted sources to prevent block evasion and framing attacks.
- NEW MAJOR FEATURE: Geo-Challenge. Added a new security layer to challenge visitors from selected countries with an invisible JavaScript test instead of a hard block. This is ideal for filtering bot traffic from high-risk regions without affecting legitimate users. The feature is fully configurable and independent of the main Geoblocking module.
- Major Enhancement: Full Bulk Actions for IP Management. The Whitelist and Blocked IPs tables now support full bulk actions. Administrators can select multiple entries to remove/unblock them at once, or unblock all IPs from all lists with a single click, dramatically improving management efficiency.
- WP-CLI Expansion: Added a comprehensive set of new WP-CLI commands to manage all new features from the command line, including
wp advaipbl trusted-proxy,wp advaipbl geo-challenge,wp advaipbl asn-whitelist, andwp advaipbl signature. - Security & UX Hardening: The JavaScript challenge page has been completely redesigned. It is now fully responsive, includes enhanced security headers (CSP), and features a more robust user interaction flow with a timeout and manual verification option.
- Fix: Resolved a critical bug where the JavaScript challenge could enter an infinite loop on sites with aggressive page caching or cookie consent (RGPD/GDPR) plugins. The system is now significantly more compatible with these environments.
- Fix: Corrected a bug in WP-CLI where the
session listcommand would cause a fatal error due to a missing dependency. - Fix: Patched a compatibility issue with WP-CLI on servers running PHP versions older than 8.1, preventing fatal errors when using geolocation-dependent commands.
- Code Quality: Major Refactor. The main plugin class (
class-advaipbl-main.php) has been significantly refactored. All UI rendering logic has been moved to a new dedicated class (class-advaipbl-admin-pages.php), separating concerns and making the codebase much more maintainable and scalable for future development.
8.5.7
- NEW FEATURE: Endpoint Lockdown for Login Page. The automated Endpoint Lockdown defense now protects
wp-login.phpfrom distributed brute-force attacks. - NEW FEATURE: ASN Whitelist. You can now whitelist entire networks (ASNs) like Google or Cloudflare to prevent false positives.
- Major Fix: Race Condition Elimination. Refactored the IP blocking mechanism with an atomic, database-level locking system to prevent duplicate blocks during high-frequency attacks.
- Security Hardening: Implemented anti-spoofing intelligence to correctly block attackers faking their IP as
127.0.0.1. - Fix: Resolved a bug where the admin dashboard counter could become out of sync on sites with persistent object caching.
- Fix: Corrected a bug causing a fatal error on WP-CLI when used on servers with a CLI PHP version older than 8.1.
- Enhancement: Redesigned the main “Settings” page with a side navigation menu and modern toggle switches.